In today’s digital world, safeguarding your internet connection is more important than ever. One of the most effective tools for protecting your online activities is a firewall. Whether you’re a home user or managing a business network, understanding how to use a firewall effectively can significantly enhance your internet security. This guide will walk you through the essential steps and best practices for using a firewall to protect your internet connection.
What Is a Firewall and Why Is It Important?
Before delving into configuration and usage, it’s crucial to understand what a firewall does and why it’s essential for internet protection.
1. Understanding Firewalls
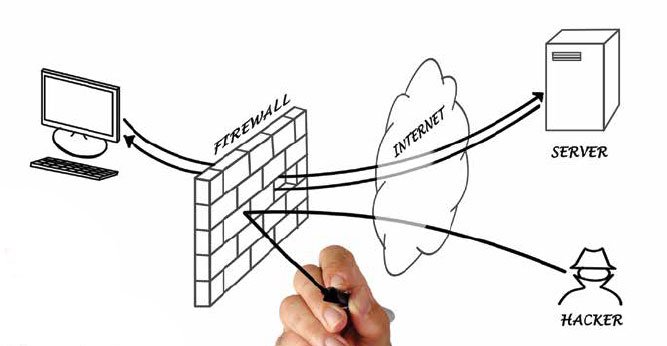
A firewall acts as a gatekeeper between your computer or network and the internet. It filters incoming and outgoing traffic based on predefined security rules. This helps prevent unauthorized access and blocks potentially harmful traffic.
2. Importance of Firewalls
Firewalls are essential for defending against cyber threats such as malware, hackers, and other malicious attacks. They provide a critical layer of protection by controlling the data that enters and exits your network.
Setting Up Your Firewall
Once you understand the importance of a firewall, the next step is setting it up correctly. Here’s how you can get started.
1. Choose the Right Firewall
Selecting the right type of firewall is the first step. There are two main types:
a. Hardware Firewalls
Hardware firewalls are standalone devices that protect your entire network. They are typically used in business environments but can also be suitable for tech-savvy home users.
b. Software Firewalls
Software firewalls are installed on individual computers. They are often included in comprehensive security suites and are ideal for personal use or small offices.
2. Install and Configure Your Firewall
Once you’ve chosen your firewall, follow these steps to install and configure it:
a. Installation
For hardware firewalls, connect the device between your modem and router. For software firewalls, download and install the software according to the manufacturer’s instructions.
b. Basic Configuration
Configure basic settings such as allowing trusted applications and blocking unauthorized connections. Most firewalls come with default settings that provide a good starting point, but you may need to adjust them based on your specific needs.
Best Practices for Using a Firewall
Effective use of a firewall involves more than just installation. Here are some best practices to ensure optimal protection.
1. Regularly Update Firewall Rules
Keeping your firewall rules updated is crucial for maintaining security. Cyber threats are constantly evolving, so your firewall’s rules need to reflect the latest threat intelligence.
a. Review and Adjust Rules
Regularly review and adjust your firewall rules to ensure they align with current security needs. Remove rules for outdated applications and add new ones for emerging threats.
b. Enable Automatic Updates
Where possible, enable automatic updates for your firewall software to ensure you receive the latest security patches and improvements.
2. Monitor Firewall Logs
Monitoring firewall logs helps you track what traffic is being allowed or blocked. This can provide valuable insights into potential security issues.
a. Review Logs Regularly
Regularly review the logs to identify any unusual activity. Look for patterns or anomalies that might indicate a security threat.
b. Adjust Settings Based on Logs
Use insights from the logs to adjust your firewall settings. For example, if you notice frequent blocked attempts from a specific IP address, you might want to investigate further.
3. Test Your Firewall’s Effectiveness
Testing your firewall is essential to ensure it’s working as intended. Conduct regular tests to verify that it’s effectively blocking unauthorized traffic and allowing legitimate connections.
a. Use Security Testing Tools
Utilize security testing tools to simulate various attack scenarios. This helps you understand how well your firewall can handle potential threats.
b. Perform Regular Vulnerability Scans
Regularly perform vulnerability scans on your network to identify and address any weaknesses in your firewall configuration.
Conclusion
Using a firewall effectively is a cornerstone of robust internet protection. By understanding its role, choosing the right type, configuring it properly, and following best practices, you can significantly enhance your security against online threats. Regular updates, monitoring, and testing are key to maintaining a secure network environment. With the right approach, a firewall can be a powerful tool in safeguarding your online activities and data.